IT Compliance Management: The What and Why

IT Compliance Management: The What and Why December 5, 2018 Compliance | Corporate Security | Cyber Security | Cyber Threats | Regulatory Compliance | Risk Assessment & Compliance | RiskWatch Blog IT Compliance Management IT compliance management can be difficult for many organizations that don’t understand the requirements of cyber data, especially when you have […]
A Closer Look at IT Compliance

A Closer Look at IT Compliance September 26, 2018 Compliance | Cyber Security | Cyber Threats | Risk Assessment & Compliance | Threat Assessment | Uncategorized Importance of Implementing IT Compliance With the vast majority of businesses going digital, IT compliance is now more prevalent than ever. With that said, we wanted to utilize this […]
How to Prepare for a Security Audit

How to Prepare for a Security Audit August 22, 2018 Compliance | Corporate Security | Cyber Security | Cyber Threats | Emergency Preparedness | Facilities Security | HIPAA Risk Analysis | OSHA | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Uncategorized The Unnecessary Torture of Security Audits From financial services to […]
Five Unique Cyber Threats that You may not have Considered

Five Unique Cyber Threats that You may not have Considered August 7, 2018 Cyber Security | Cyber Threats | Identity Theft | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized The Unnecessary Torture of Security Audits From financial services to healthcare, nearly every […]
Financial Service Risks That Require a Powerful Risk Assessment Platform

Financial Service Risks That Require a Powerful Risk Assessment Platform July 23, 2018 Compliance | Cyber Security | Cyber Threats | Disaster Recovery Planning | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized Financial Service Risk Over the last several years, the financial […]
Top Five Vendor Risks

Top Five Vendor Risks June 18, 2018 Compliance | Cyber Security | Cyber Threats | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Third Party Risks | Uncategorized A vendor can be defined as a person or a company that offers some service or product for a fee. Many companies hire third-party […]
Information Risk: ISO 27001

Information Risk: ISO 27001 May 30, 2018 Compliance | Cyber Security | Cyber Threats | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment What is it? ISO 27001 is an international standard that provides a process for an Information Security Management System (ISMS). An ISMS is […]
How Consulting Firms Can Provide Better Service at a Lower Cost
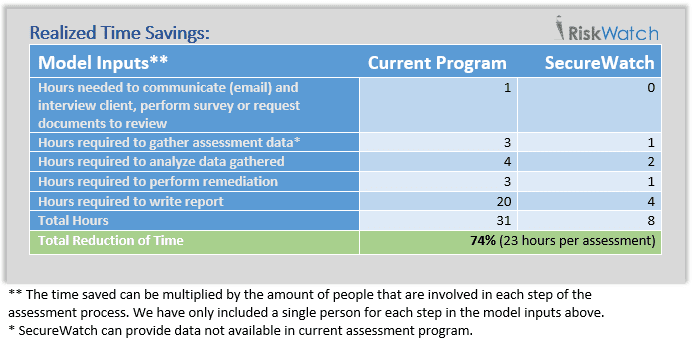
How Consulting Firms Can Provide Better Service at a Lower Cost May 17, 2018 Compliance | Cyber Security | Cyber Threats | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized Risk consultants are so busy managing risk for other companies that they often […]
Five Must Knows About GDPR

Five Must Knows About GDPR April 18, 2018 Compliance | Cyber Security | Cyber Threats | Disaster Recovery Planning | Identity Theft | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Uncategorized What is GDPR? A trending topic these days is the latest data regulation that businesses […]
SEC Cybersecurity Threats

SEC Cybersecurity Threats April 24, 2014 Corporate Security | Cyber Security | Cyber Threats | Risk Assessment The Securities and Exchange Commission (SEC) to require registered broker-dealers and registered investment advisers to conduct risk assessments to identify cybersecurity threats, vulnerabilities, and potential business consequences. Earlier this year on March 26, 2014, the U.S. Securities and […]
