Diversity and Inclusion in the Workplace
Diversity and Inclusion in the Workplace June 11, 2020 Compliance | Diversity | Regulatory Compliance | Riskwatch Blog Diversity and Inclusion As we settle into the middle of Pride Month and protests across the world call out systemic racism, it feels appropriate that we use this time to address the importance of diversity and inclusion […]
Ohio Gas Company Fined $400k for Gas Line Rupture

Ohio Gas Company Fined $400k for Gas Line Rupture March 13, 2019 Compliance | Managing the Risk Assessment | Regulatory Compliance | Riskwatch Blog Gas Company Noncompliance Causes Ruptured Gas Line Two weeks ago, PUCO (Public Utilities Commission of Ohio) fined Columbia Gas $400,000 for failure to comply with set operating procedures in abandoning a service line […]
IT Compliance Management: The What and Why

IT Compliance Management: The What and Why December 5, 2018 Compliance | Corporate Security | Cyber Security | Cyber Threats | Regulatory Compliance | Risk Assessment & Compliance | RiskWatch Blog IT Compliance Management IT compliance management can be difficult for many organizations that don’t understand the requirements of cyber data, especially when you have […]
Top Five Risks in the Oil & Gas Industry

Top Five Risks in the Oil & Gas Industry September 12, 2018 Compliance | Corruption | OSHA | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Uncategorized | Workplace Violence Prevention The Dangers of the Oil and Gas Industry The oil and gas industry easily has a large impact on the mass […]
How to Prepare for a Security Audit

How to Prepare for a Security Audit August 22, 2018 Compliance | Corporate Security | Cyber Security | Cyber Threats | Emergency Preparedness | Facilities Security | HIPAA Risk Analysis | OSHA | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Uncategorized The Unnecessary Torture of Security Audits From financial services to […]
Five Unique Cyber Threats that You may not have Considered

Five Unique Cyber Threats that You may not have Considered August 7, 2018 Cyber Security | Cyber Threats | Identity Theft | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized The Unnecessary Torture of Security Audits From financial services to healthcare, nearly every […]
Financial Service Risks That Require a Powerful Risk Assessment Platform

Financial Service Risks That Require a Powerful Risk Assessment Platform July 23, 2018 Compliance | Cyber Security | Cyber Threats | Disaster Recovery Planning | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized Financial Service Risk Over the last several years, the financial […]
Top Five Vendor Risks

Top Five Vendor Risks June 18, 2018 Compliance | Cyber Security | Cyber Threats | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Third Party Risks | Uncategorized A vendor can be defined as a person or a company that offers some service or product for a fee. Many companies hire third-party […]
Information Risk: ISO 27001

Information Risk: ISO 27001 May 30, 2018 Compliance | Cyber Security | Cyber Threats | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment What is it? ISO 27001 is an international standard that provides a process for an Information Security Management System (ISMS). An ISMS is […]
How Consulting Firms Can Provide Better Service at a Lower Cost
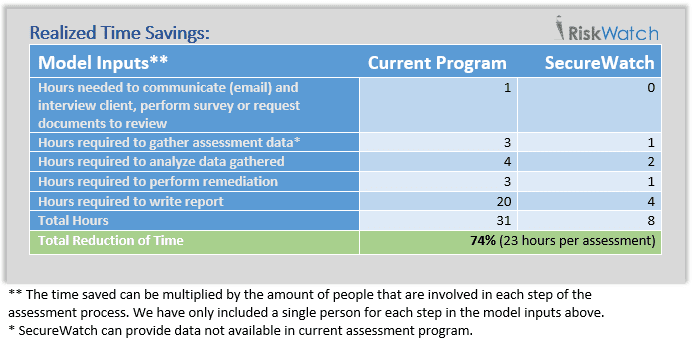
How Consulting Firms Can Provide Better Service at a Lower Cost May 17, 2018 Compliance | Cyber Security | Cyber Threats | Managing the Risk Assessment | Regulatory Compliance | Risk Assessment | Risk Assessment & Compliance | Threat Assessment | Uncategorized Risk consultants are so busy managing risk for other companies that they often […]
