Companies struggle to complete assessments in a thorough and timely manner, due to issues in training, analyzing data, and implementing changes. Protecting your assets, preventing costly penalties, and maintaining your reputation are major challenges for all involved.
External Security Audits
Sign up for instant access to a free trial.

The Challenges
Companies have a multitude of reasons for receiving or performing an external security audit, ranging from standard security practices to meeting third-party requirements. Passing an audit by a third party includes many challenges, mainly centered around the areas that will be audited. This requires an internal audit that will first identify required compliance, any security gaps, and remedial tasks.
The Impact
Customers have reported a previous inability to fully manage their audit preparation due to an unorganized process that ultimately left them with security gaps or compliance findings and in breach of contract. Often, a single failed audit is enough to severe a partnership or warrant a fine by governing bodies.
Without a reliable platform to streamline assessments and automate key functions such as report writing and data analysis, these customers were struggling to complete their required assessments prior to external audits. In addition, these audit requirements benefited the company, meaning non-compliance left numerous security gaps and vulnerabilities.
Noncompliance and gaps in security leave your organization vulnerable to attacks and penalties, ultimately limiting growth and damaging company reputation.
Achieve your Security Audit Goals with RiskWatch
Central Repository
- Streamlines processes and eliminates redundancies with transferring data.
- Centralizes the storage and maintenance of data.
- Generate a higher ROI by eliminating costs of poor data quality, erroneous information, and uninformed decision making.
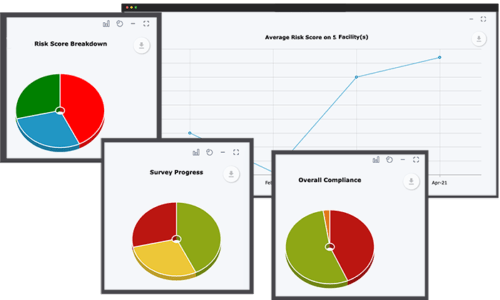

Automated Reporting
- Save an average of 16 hours per report.
- View robust data from multiple sources within a single place.
- Increase transparency with any data available in any format, on demand.
Data Collection Portal
- Create custom landing pages for your data collection portals, using custom colors or instructions.
- Eliminate training time by sending out a limited-view collection page.
- Assessments to a portal can be created just once and used repeatedly, eliminating unnecessary work.
Product Overview
[pafe-template id=”28252″]
[pafe-template id=”28260″]
[pafe-template id=”28266″]
[pafe-template id=”28268″]
[pafe-template id=”28269″]











