Spear Phishing
What is Spear Phishing?
Spear phishing is a means of electronic communication, most commonly via email, that is targeted to a specific individual or business in an attempt to steal private information from the party, such as login credentials or financial information. The goal of this messaging is to usually to get the recipient to click on a malicious link or attachment. Although the primary purpose is to steal data, the attackers may also intend to install malware on the victim’s system.
Spear phishing differs from regular phishing attacks by the method of targeting. Phishing attacks will target a large number of recipients at once, mass emailing them in an attempt to succeed with a small percentage. An example of a phishing attempt is a mass email using the Amazon logo and claiming there is a problem with your recent order. This is centered on the assumption that most recipients will have recently placed an order or are curious about a mix-up.
Spear phishing, in contrast, is more targeted and attempts to deceive a single individual or small group at a time. The attackers will use publicly available information to make their messaging seem more authentic. An example of spear phishing is the attacker looking up information available on your LinkedIn profile, then impersonating your CEO and using your job title to ask you to start a specific project with more details described in an attachment. This is centered on using pieces of information you know to be factual and therefore increasing your trust.
Typical Spear Phishing Process
Information and awareness are some of the best tools in your security arsenal for this type of attack. Making sure employees know not to trust any email or message that ends up in their inbox is crucial. As such, we are going to layout the typical process of a spear-phishing attack and highlight important areas.
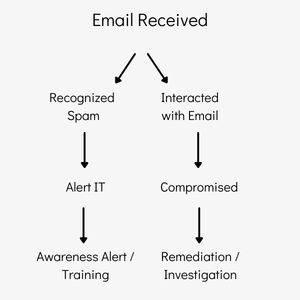
The process begins with the attacker sending an email or some type of messaging that impersonates a trustworthy source. From here there are two central potential branches: either the recipient recognizes the message as fraudulent, or perceives it as authentic. If detected as fraudulent, the recipient should then report the message to IT or security personnel, who will then generate awareness of the situation. This could be a company email reminding employees to be wary of suspicious emails, or perhaps incorporated into company training. The employee may also ignore or delete the message, but the result is still that no harm is done.
The other possibility is that the recipient trusts the message they receive, clicking on the malicious link or entering personal information on the subsequent page. As the organization is now compromised, a period of time will pass until this is noticed by staff members, either through their own efforts or by the hacker making them aware through demands. Teams will then work on an investigation and remediation. They will need to know all the information that has been accessed, how it was reached, and take the proper steps to return to a secure state.
While these paths may seem fairly straightforward, there is a lot of work involved, especially during remediation. As one of the most time-consuming tasks, your team will likely spend countless hours combing through security logs.
Anyone can fall victim to a phishing attempt, depending on the amount of effort the hacker has put in and how convincing their message is, making it important to approach each message with skepticism.
Spear Phishing Prevention
Spear phishing is an expensive cyberattack that can result in severe losses for a business. In addition to data loss and losing public trust, the financial impact can be crippling. Even tech giants Goggle and Facebook have famously been scammed out of millions of dollars through spear-phishing attacks that impersonated a computer manufacturer. According to a report by the Internet Crime Complaint Center, phishing attacks more than doubled in 2020, totaling over 240,000 complaints. These complaints reported a loss of over $5 million dollars as well. Read more here.
To best prevent spear-phishing attacks on your organization, consider the following best practices:
Employee Training – One of the most effective methods of protecting against spear phishing is to educate your employees. Spear phishing requires cooperation from an internal user, so making employees aware of these fraudulent messages reduces the likelihood of them accidentally giving an attacker access. Train them on how to check email domains, check link URLs before clicking, recognize unusual requests or suspicious wording. Go over protocol for reviewing suspicious emails with a security team member.
Use Logic – This may tie into employee training but understanding the need to stop and process what you’re reading is crucial. Who is the message from? Does it sound like a reasonable request from them? If your “CEO” is asking you to purchase a gift card or give your login credentials, that should be an easy red flag. Recognize what information you have publicly available and know any of it could be used against you. When in doubt, call the person or speak with them directly to verify. Visit websites through your browser instead of clicking direct links and utilize safe browsing practices.
Two-factor Authentication – Two-factor authorization is a great backup defense on multiple fronts. In the scenario that a user’s login information is compromised, this prevents unauthorized logins and alerts you that an attack may have occurred.
Passwords – To help protect your organization, ensure all employees practice proper password protocol. This includes basic password security such as using enough characters, ensuring your passwords are unique for each login account, and not writing passwords down. It’s now widely accepted that “passphrases” instead of using a series of random characters are more secure and help you remember your login. Passwords should also be changed on a regular basis, especially after you suspect an attack attempt. Read more on passwords here.
Update Software – Whenever possible, ensure software is updated. This protects against known weaknesses and ensures you have the latest defense working for you. This includes email filters and antivirus software. Automatic updates are very helpful. This will ensure you have screening and detection systems checking for fraudulent emails as the first line of defense.
Spear Phishing Methods
We’ve discussed what spear phishing is and have given examples, but there are several recognized methods of phishing attacks that can be used while targeting a recipient. For the sake of awareness, let’s briefly highlight these below.
Whaling: Whaling is a phishing attack that targets a high-profile person, such as a senior executive or someone with a lot of power or expected access to resources.
CEO Fraud: This phishing attack is aimed at impersonating senior executives. This is the scenario when you might get a request from your “CEO” or a director in your organization. This messaging may ask you for money, to review a document, or to provide login credentials.
Vishing: Terminology used in reference to voice phishing. Vishing occurs when a cybercriminal calls a person and attempts to make them take an action such as those previously discussed. For example, during a busy shopping period such as around Christmas, they may call and claim you need to verify a package for delivery. During tax season, a caller may impersonate the IRS claiming they need immediate payment. Vishing attempts will usually try to create a sense of urgency before suspicion sets in.
Smishing: This is a form of spear phishing that specifically utilizes text messaging as its method of delivery. Typically, the text will include a link that installs malware on the user’s device when accessed. The main red flag for these attempts will be the unrecognized number.
Clone Phishing: This approach attempts to replicate a typical email you would normally receive, copying text and images. These may go so far as to replicate websites or landing pages to trick you. For example, you may receive an email to join a Google doc are sign something on DocuSign.
Next Steps
Protecting against and remediating spear-phishing attacks can be an overwhelming process. It involves analyzing and reviewing massive amounts of data, using AI and automation technologies, reviewing and creating internal policies, and more. Utilize RiskWatch to help reduce the strain of this process.